What is SSH (Secure Shell) and How to connect EC2 instances in AWS using SSH.
Table of contents
What is SSH
SSH is also known as Secure Shell or Secure Socket Shell It is a secure way to access a computer over an unsecured network. It is a cryptographic network protocol that allows two computers to communicate and share data over an insecure network such as the Internet.
To understand SSH, let's go back to the time when there was no SSH, Connecting two computers over the internet was still possible using other protocols but they had major security issues, like any man in the middle can intercept messages.
Before SSH:
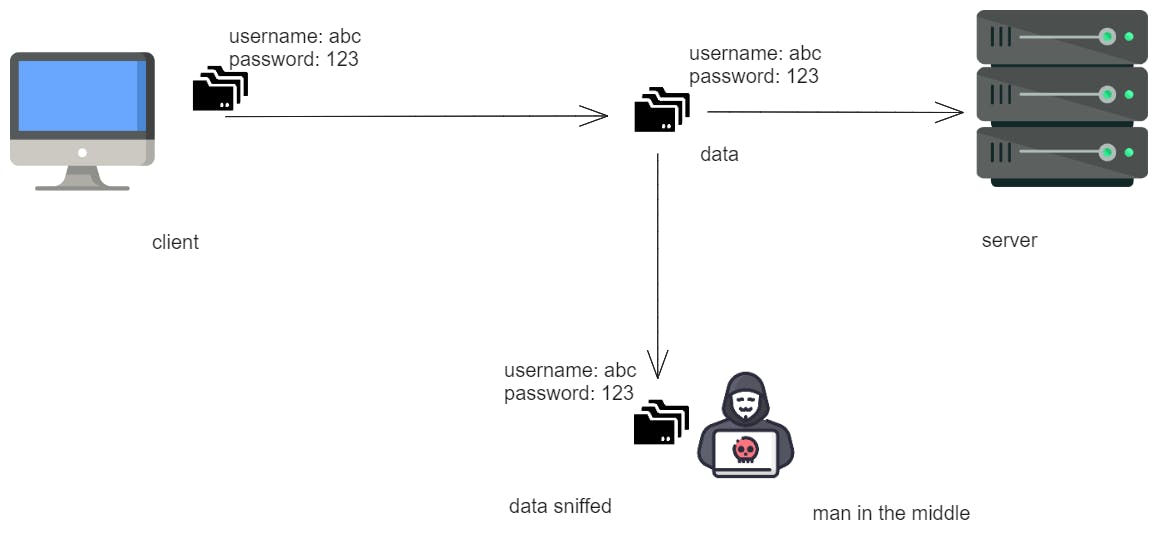
After SSH:
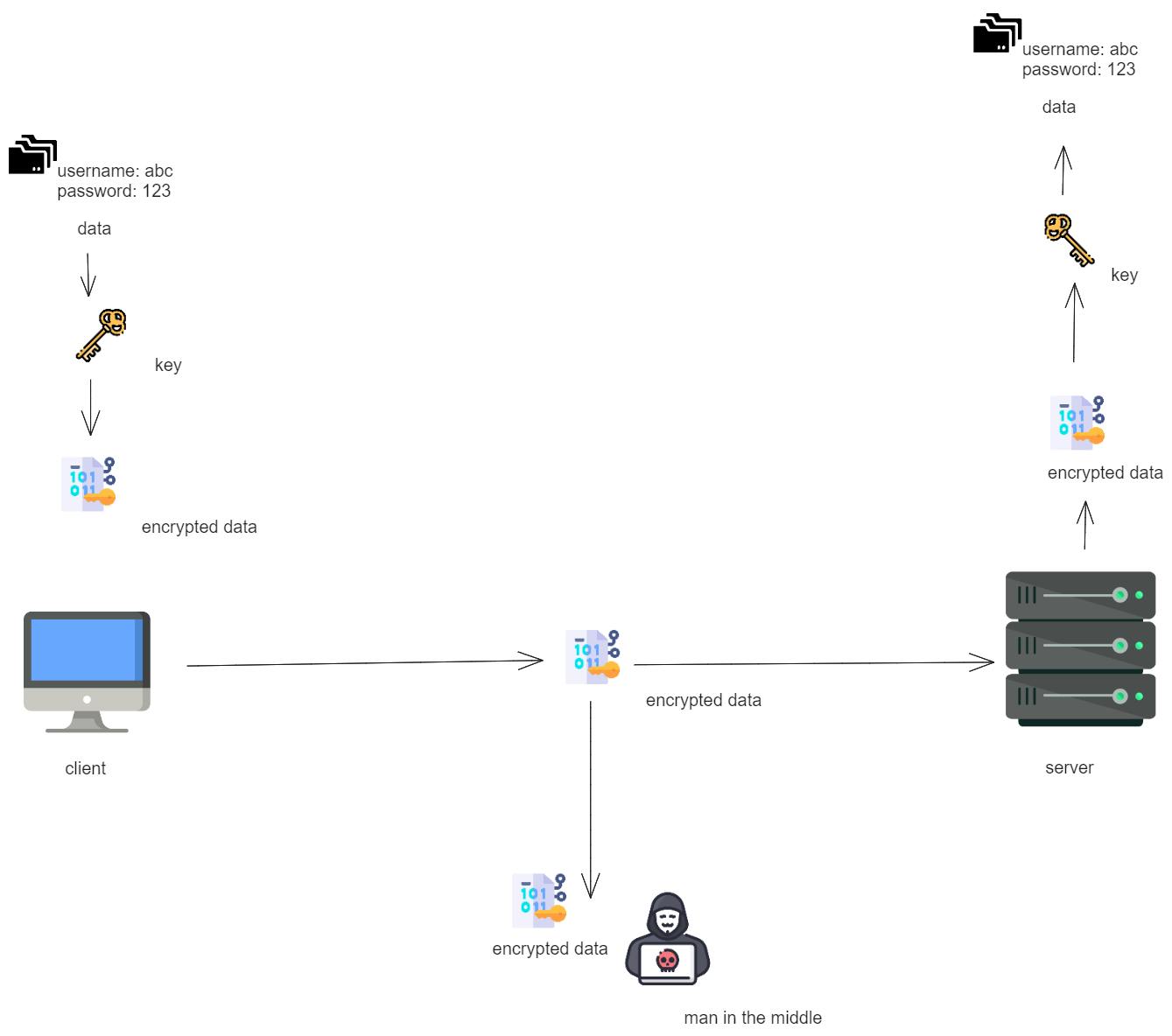
SSH Encryption Techniques:
SSH uses 3 different types of encryption techniques,
Symmetrical Encryption
Asymmetrical Encryption
Hashing
Symmetrical Encryption:
Symmetric encryption methods rely on a single key for both encrypting and decrypting messages exchanged between parties. This approach is often referred to as shared key encryption because both devices utilize an identical key for encrypting their transmitted data and decrypting the data they receive.
This cryptographic approach safeguards the complete SSH connection, thwarting potential man-in-the-middle attacks. However, a challenge emerges during the initial key exchange. In this scenario, if a third party is present during the key exchange, they may gain access to the key and consequently, the entire message.
To address this issue, a Key Exchange algorithm comes into play. This algorithm facilitates the secure exchange of secret keys, ensuring that they remain confidential and inaccessible to any potential interceptors.
The implementation of the key exchange algorithm necessitates the use of asymmetric encryption techniques.
Asymmetrical Encryption
In asymmetric encryption, two distinct keys, namely the private and public keys, serve the roles of encryption and decryption. The private key remains exclusive to the user and must not be divulged to any other party, while the public key is openly shared. The public key is stored on the SSH server, whereas the private key resides locally on the SSH client, constituting a key pair. Messages encrypted with the public key can only be decrypted using the corresponding private key.
This method offers enhanced security, as even if a third party obtains the public key, they lack the means to decrypt the message due to their lack of knowledge of the private key.
Asymmetrical encryption does not encompass the entirety of the SSH session's encryption. Instead, it predominantly serves the purpose of the key exchange algorithm for symmetric encryption. In this process, both systems (client and server) temporarily generate public-private key pairs prior to establishing a connection. Subsequently, they share their private keys to create a shared secret key.
Upon the establishment of a secure symmetric connection, the server employs the public key for transmission to the client for authentication purposes. The client can only decrypt the data if it possesses the private key, thereby facilitating the establishment of the SSH session.
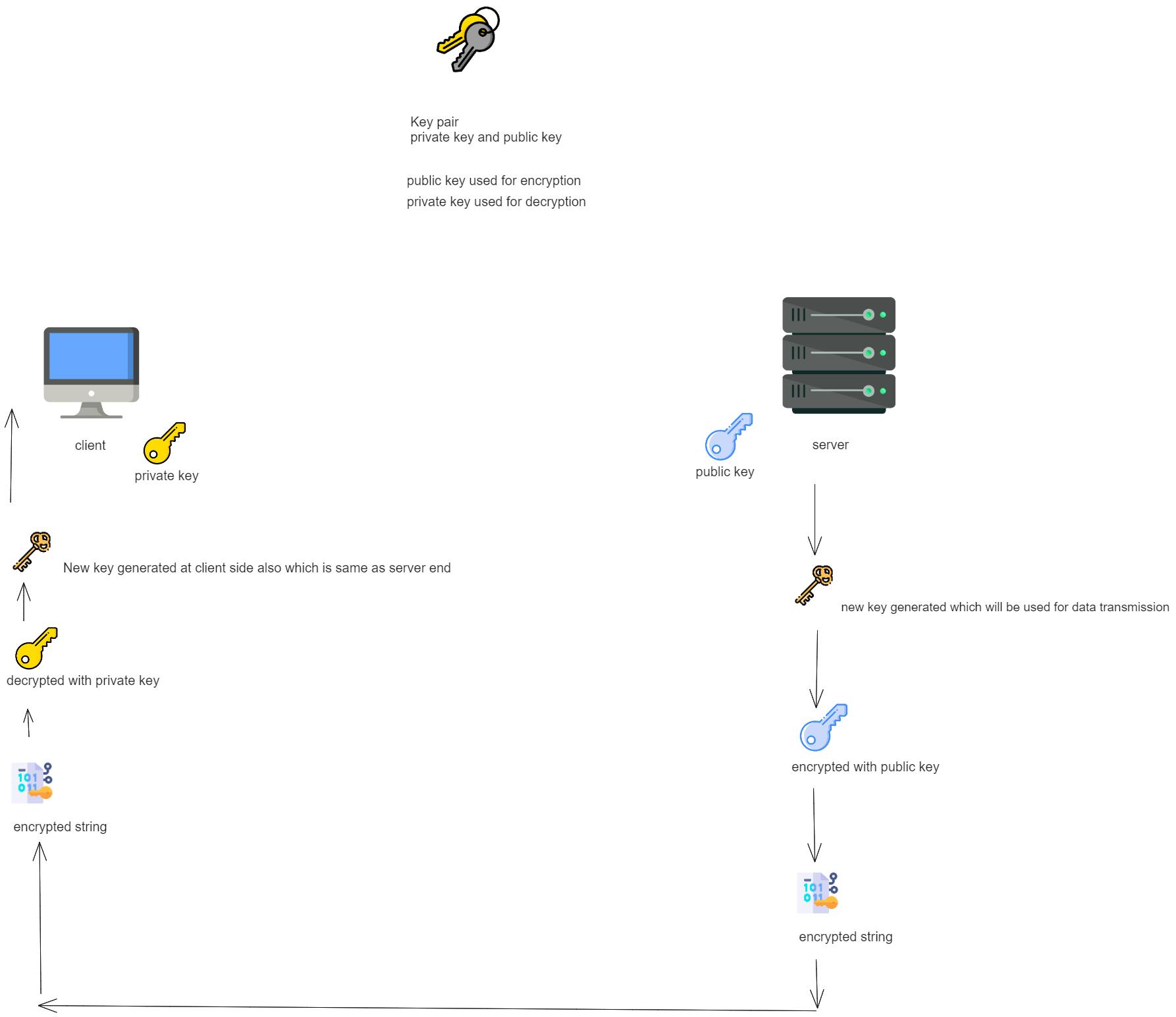
Hashing
In SSH, one-way hashing is used as the encryption technique, which is another form of cryptography. The hashing technique is different from the above two methods, as it is not meant by decryption. It generates the signature or summary of information. SSH uses HMAC(Hash-based Message authentication) to ensure that messages are reached in complete and unmodified form.
In this technique, each transmitted message must have a MAC, which uses three components: symmetric key, packet sequence number, and message content. These three components form the hash function that generates a string that doesn't have any meaning, and this string is sent to the host. The host also has the same information, so they also generate a hash function, and if the generated hash matches with the received hash, it means the message is not tempered.
Workings of SSH
The SSH protocol operates on a client-server model, facilitating a secure connection between a secure shell client application (where the session is displayed) and the SSH server (where the session executes).
As previously mentioned, SSH was initially developed to replace insecure login protocols such as Telnet and rlogin, serving the same fundamental purpose.
The primary function of SSH is to establish a connection to a remote system for a terminal session. To achieve this, the following command is utilized:
shellCopy codessh UserName@SSHserver.xyz.com
This command allows the client to connect to the server named server.xyz.com using the provided UserName.
When connecting for the first time, SSH will prompt the user with the remote host's public key fingerprint and seek confirmation. The following message will appear:
shellCopy codeThe authenticity of host 'sample.ssh.com' cannot be established.
DSA key fingerprint is 01:12:15:89:89:ab:cd:ei:sf:fe:dc:bc:90:76:54:32:00.
Are you sure you want to continue connecting (yes/no)?
To proceed with the session, the user must choose either "yes" or "no." Selecting "yes" will store the host key in the local system's known_hosts file. By default, this key is concealed within the hidden file located at ~/.ssh/known_hosts in the user's home directory. Once the host key is stored in this hidden file, no further approval is required, as the host key will automatically authenticate subsequent connections.
Connecting to AWS EC2 using SSH
To Connect to your EC2 instances using SSH, Go to your AWS console and then go to EC2 Dashboard and select the instance you want to connect.
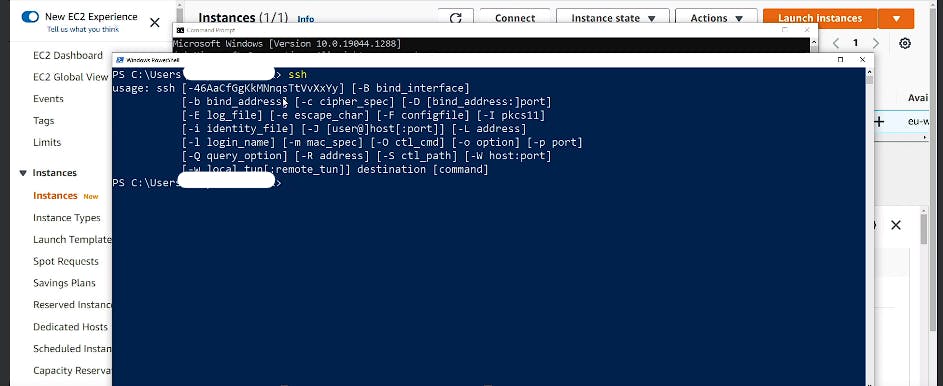
but before that check if your client machine has SSH or not, if you are using Windows, open Powershell or command prompt and run ssh command and if your screen looks like below then you have SSH on your system. If not then you can use putty for the same.
If you have not downloaded the .pem file (Access keys) then go ahead and create and download the files.
Then in the PowerShell Window, go into the directory where your .pem file is located.
Please also make sure you have port 22 open from the security groups for your EC2 to use SSH.
next enter ssh -i .\xyz.pem username@public ip of the EC2 instance
Now you are connected to your EC2 instance.
If you asked for the confirmation for permission issue then say YES to run your command. Then you can later change the owner of the file to remove the permission issue. you need to be the only owner of the .pem file and no one needs to have access to that file. You can change this from your file properties under security.

